After the first post regarding unifi, I was doing some experiment with my unifi network setup. As thing goes along , I had to admit thing turn out very scary after found out this.
First of all :
1. remote management is enabled by default.
– this also enabled the following
i. web management on default port 80
ii. SSH at default port 22
iii. telnet at default port 23.
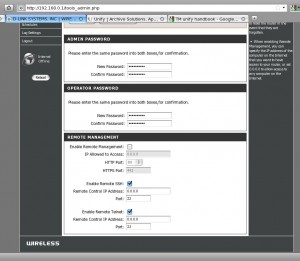
2. User’s being given the “admin” account detail on the router.
at first , I was assuming this is the only account available..
Later , I found out that there is another account exist
with higher roles admin account .. ~ .”operator”
which is having access to SSH , telnet and also web interface.
– if using “admin” account , you can only disable the “web management – remote admin”
while “SSH and TELNET “.. remained invisible and enabled.. !
you can change the password of “admin” to whatever but the user “operator”
still having the original password set by “telekom”
– it can be either your username in reverse order . or “telekom”.
3. WIFI ESSID is your unifi username !!
– so anyone who drive thru your home, and did a scan.. one can easily get the your username . ~ i.e user@unifi.
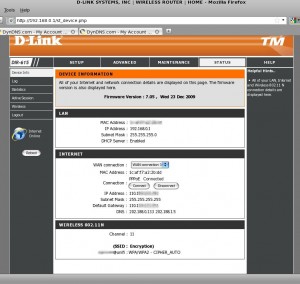
4. the HTTP password is stored in plain text .. !
– is not a MD5 or whatsoever.
– just SSH/telnet to the router and
ssh -l operator 192.168.0.1
# cat /var/etc/httpasswd
operator:xxxxx
admin:xxxxx
# cd /var/etc/
# cat passwd
operator:xxxxxxxx:0:0:operator:/:/bin/sh
# cat stunnel.conf
cert = /etc/stunnel_cert.pem
key = /etc/stunnel.key
pid = /var/run/stunnel.pid
setuid = 0
setgid = 0
debug = 7
output = /var/log/stunnel.log
[https]
accept = 443
connect = 127.0.0.1:80
5. wah ! brilliant … it treating whatever connected via 443 as 127.0.0.1
so anyone having unifi at home.. auth for once.. can login to any other unifi router running on HTTPS mode without any password.
– which is enabled by default for unibiz type !!
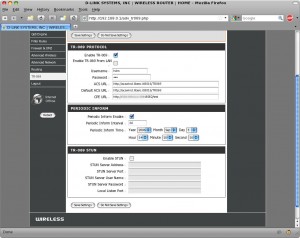
6. It has something called “TR-069” which did phoning TM every 60 days or so,
for config repository / sync ??
– and was having publishing the content on this router as well.
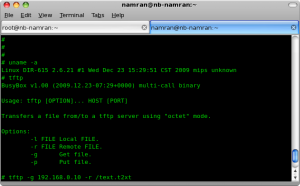
7. the Busybox inside the router is having tftpd client .
which can talk to another tftpd server to send out/in file from/to the router .. !!
* note : to send out file from this router.. it must have the file exist on destination first.. which could be done by simply touch the file on destination before transfer with the following command.
# tftp -p 192.168.0.10 -l -r /text.t2xt
Hmmm.. mangling around ..
# cat config.sh
#!/bin/sh
image_sign=`cat /etc/config/image_sign`
case "$1" in
start)
echo "Mounting proc and var ..."
mount -t proc none /proc
mount -t ramfs ramfs /var
mkdir -p /var/etc /var/log /var/run /var/state /var/tmp /var/etc/ppp /var/etc/config /var/dnrd /var/etc/iproute2
echo -n > /var/etc/resolv.conf
echo -n > /var/TZ
echo "127.0.0.1 hgw" > /var/hosts
#Added by Lin-Siong Pui for SSH, 20090406
mount -t devpts devpts /dev/pts
# if no PIN, generate one
#pin=`devdata get -e pin`
#[ "$pin" = "" ] && devdata set -e pin=`wps -g`
# prepare db...
echo "Start xmldb ..." > /dev/console
xmldb -n $image_sign -t > /dev/console &
sleep 1
#Modify by Lin-Siong Pui for alpha falsh agent, 2009-06-22
#/etc/scripts/misc/profile.sh get
/etc/scripts/misc/profile.sh init
/etc/templates/timezone.sh set
/etc/templates/logs.sh
sleep 1
logger -p 192.1 "SYS:001"
# bring up network devices
ifconfig lo up
env_wan=`devdata get -e wanmac`
[ "$env_wan" = "" ] && env_wan="00:00:FF:FF:FF:xx"
ifconfig eth2 hw ether $env_wan up
rgdb -i -s /runtime/wan/inf:1/mac "$env_wan"
PANIC=`rgdb -i -g /runtime/func/panic_reboot`
[ "$PANIC" != "" ] && echo "$PANIC" > /proc/sys/kernel/panic
TIMEOUT=`rgdb -g /nat/general/tcpidletimeout`
[ "$TIMEOUT" = "" ] && TIMEOUT=7200 && rgdb -s /nat/general/tcpidletimeout $TIMEOUT
echo "$TIMEOUT" > /proc/sys/net/ipv4/netfilter/ip_conntrack_tcp_timeout_established
# Setup VLANs
vconfig set_name_type DEV_PLUS_VID_NO_PAD > /dev/console
# Disable temporarily, need to find a good location to activate web deamon.
# Start up LAN interface & httpd
# ifconfig br0 0.0.0.0 up > /dev/console
# /etc/templates/webs.sh start > /dev/console
mkdir /var/etc/iproute2
chmod 0755 /var/etc/iproute2
echo "" >> /var/etc/iproute2/rt_tables
echo "" >> /var/etc/iproute2/rt_scopes
echo "" >> /var/etc/iproute2/rt_realms
echo "" >> /var/etc/iproute2/rt_protos
echo "" >> /var/etc/iproute2/rt_dsfield
chmod 0644 /var/etc/iproute2/*
;;
stop)
umount /tmp
umount /proc
umount /var
;;
esac
#
# cd /etc/
# ls
tr069_key.pem templates snmp passwd group config
tr069_cert.pem stunnel_cert.pem scripts iproute2 ethertypes TZ
tr069_ca.pem stunnel.key resolv.conf init.d dropbear RT3052_AP_2T2R_V1_1.bin
tlogs stunnel.conf ppp hosts defnodes
#
Huh.. it had the default firmware inside too !!
in case you need it for whatever case..
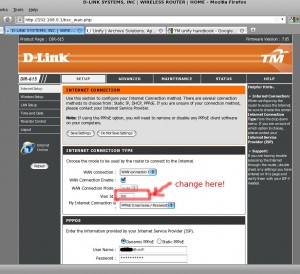
one thing that could be done before completely replace this router with the new one.
re-assign the VLAN ID to another bridge interface such as “WAN Connection 3” .
and setup custom router from there..
p/s : .. yes, might need to re-word the previous blog post as … F**k “telekom”.. !!

How to remote access the unifi router? Have to know the router wan IP address. How to detect neighbour’s router wan IP?
Go subscribe your own Unifi la bro. Tak malu nak mencuri jiran punya hahaha
basically follow the link to the YouTube video down the page that highlights using the Megapolis hack
program in addition to where you can get it.
megapolis cheats at http://www.youtube.com/watch?v=UFZXhUkRyh4
I’m now not sure the place you are getting your information, however good topic. I needs to spend a while studying much more or figuring out more. Thank you for excellent information I was searching for this information for my mission.
Good day! I could have sworn I’ve visited your blog before but after browsing through a few of the posts I realized it’s new to me.
Regardless, I’m definitely happy I discovered it and I’ll be bookmarking it
and checking back often!
Please let me know if you’re looking for a author for your weblog. You have some really great articles and I feel I would be a good asset. If you ever want to take some of the load off, I’d
absolutely love to write some content for your blog in
exchange for a link back to mine. Please send me an email if interested.
Kudos!
I read this article completely on the topic of the resemblance of newest
and preceding technologies, it’s awesome article.
It’s very trouble-free to find out any matter on net as compared to books, as I found this article at this web page.
Hello everyone, it’s my first visit at this website,
and post is genuinely fruitful in favor of me, keep up posting these articles or
reviews.
“Spam”
salam,
mohon bantuan cara untuk masukkan no-ip @ lain2 ddns yg free
dlink dah takleh free
https://uploads.disquscdn.com/images/dca91935cd9f5bc969b0d69ee79757c3e98f6aa1daa36509d61306ef1035e750.jpg
Hey there! Do you know if they make anyy plugins to protedct against hackers?
I’m kinda paranoid about loing everything I’ve worked
hard on. Any tips? https://www.Waste-Ndc.pro/community/profile/tressa79906983/
Hi there, i read your blog occasionally and i own a similar one
and i was just curious if you get a lot of spam responses?
If so how do you reduce it, any plugin or anything you can suggest?
I get so much lately it’s driving me mad so any help is very much appreciated. https://www.uniladtech.com/news/tech-news/man-spent-10000-bitcoin-two-pizzas-worth-144371-20241205
I am actually grateful to the owner of this site who has shared this great article at here. https://wakelet.com/wake/AHg8nvKCZ0XP7TFKGAEvs
What’s up, yes this piece of writing is truly fastidious and I have learned lot
of things from it concerning blogging. thanks. https://prostata-hifu.mystrikingly.com/